Microsoft SentinelSIEM
Cloud-native SIEM & SOAR platform. Intelligent security analytics and automated response for modern threats with AI-powered threat detection across your entire environment.
Microsoft Sentinel
Intelligent security analytics for comprehensive threat detection and automated response across your entire digital estate
50B+
Events Daily
150+
Connectors
80%
Faster Detection
24/7
Protection
AI-Powered Detection
Machine learning algorithms identify sophisticated threats and reduce false positives by 90%
Automated Response
SOAR capabilities orchestrate responses across your security stack in seconds, not hours
Cloud-Native Scale
Auto-scaling infrastructure handles petabytes of data without management overhead
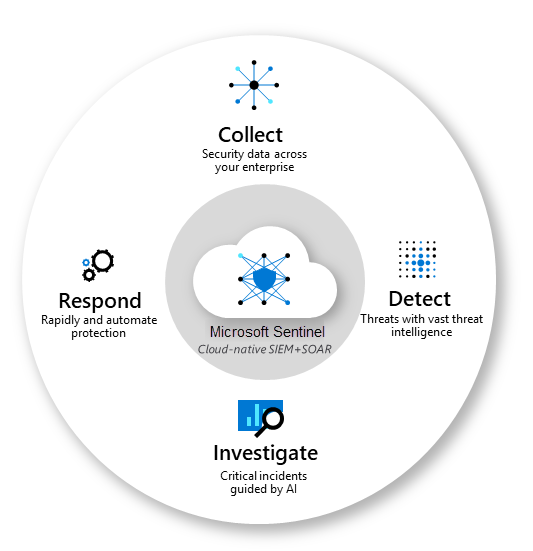
Unified Security Operations Platform
Collect
Ingest data at cloud scale
Detect
Identify threats with AI
Investigate
Hunt and analyze incidents
Respond
Automate remediation
Data Sources
Connect any data source with 150+ native connectors and custom integration options
Automation
500+ pre-built playbooks for automated threat response and remediation
Global Threat Intel
Microsoft's threat intelligence from trillions of daily signals
Core Capabilities
Intelligent Security Analytics
Leverage AI and machine learning to detect threats across your entire environment. Microsoft Sentinel uses advanced analytics to identify suspicious activities, anomalies, and patterns that traditional security tools might miss.
Cloud-Native SIEM
Built for the cloud from the ground up, Microsoft Sentinel eliminates the infrastructure overhead of traditional SIEM solutions. Scale automatically based on your data ingestion needs without managing servers or storage.

Security Orchestration & Automated Response
Automate routine security tasks and responses with built-in SOAR capabilities. Create custom playbooks using Azure Logic Apps to orchestrate responses across your security tools and accelerate incident resolution.

Comprehensive Data Connectors
Connect and collect data from across your enterprise with 150+ built-in connectors. Ingest security events from Microsoft services, third-party security tools, operating systems, network devices, and cloud platforms.
Advanced Threat Intelligence
Leverage Microsoft's global threat intelligence network to enrich your security data. Benefit from insights gathered from trillions of signals processed daily across Microsoft's ecosystem and security partnerships.
Interactive Investigation & Hunting
Use Jupyter notebooks and KQL (Kusto Query Language) for advanced threat hunting and investigation. Visualize attack patterns, create custom queries, and collaborate with your security team using familiar tools.
Security Operations Center (SOC) Capabilities
Incident Management
Streamline incident response with automated case management, assignment workflows, and collaboration tools. Track incidents from detection to resolution with full audit trails and metrics.
Investigation Workbooks
Use interactive Azure Monitor workbooks to visualize and analyze security data. Create custom dashboards, reports, and investigation workflows tailored to your organization's needs.
Threat Hunting
Proactively hunt for threats using advanced query capabilities and machine learning insights. Leverage built-in hunting queries and create custom searches to identify sophisticated attacks.
User and Entity Behavior Analytics
Monitor user and entity behaviors to detect insider threats and compromised accounts. Use machine learning to establish baselines and identify deviations that indicate potential security risks.
Security Orchestration
Automate security workflows and responses with Logic Apps integration. Connect to hundreds of services and tools to create sophisticated automation playbooks for common security scenarios.
Multi-Workspace Management
Manage multiple Sentinel workspaces from a central location. Perfect for MSSPs, large enterprises, or organizations with distributed security operations requirements.
AI and Machine Learning Capabilities
Fusion Detection Technology
Advanced machine learning correlates low-fidelity signals into high-confidence security incidents. Fusion reduces alert fatigue by combining multiple weak indicators into actionable insights.
Anomaly Detection
Built-in machine learning models detect anomalies in user behavior, network traffic, and system activities. Automatically adapt to your environment's normal patterns and identify deviations.
Threat Intelligence Integration
Automatically enrich security events with threat intelligence feeds from Microsoft and third-party sources. Match indicators of compromise against your environment's activity in real-time.
Custom Machine Learning
Build and deploy custom machine learning models using Azure Machine Learning integration. Create domain-specific detection algorithms tailored to your organization's unique risk profile.
Integration with Microsoft Ecosystem
Microsoft 365 Integration
Native integration with Microsoft 365 Defender, Azure AD, Office 365, and other Microsoft security services. Get unified visibility across your Microsoft ecosystem without additional configuration.
Azure Native Services
Built on Azure foundation with seamless integration to Azure Security Center, Azure AD Identity Protection, and Azure Monitor. Leverage existing Azure investments and skills.
Third-Party Connectors
Connect to leading security vendors including Palo Alto Networks, Check Point, Fortinet, AWS, and Google Cloud. Use CEF, syslog, REST APIs, and custom connectors for flexible integration.
On-Premises Integration
Collect security events from on-premises infrastructure using Azure Arc, log analytics agents, and syslog forwarders. Maintain visibility across hybrid and multi-cloud environments.
Common Use Cases
Multi-Cloud Security Monitoring
Centralize security monitoring across AWS, Azure, Google Cloud, and on-premises environments with unified dashboards and correlation rules.
Compliance and Auditing
Meet regulatory requirements with built-in compliance templates, automated reporting, and audit trails for SOX, PCI-DSS, HIPAA, and more.
Insider Threat Detection
Use UEBA capabilities to detect suspicious user activities, privilege escalation, and data exfiltration attempts by insiders.
IoT Security Monitoring
Monitor and secure IoT devices and operational technology environments with specialized connectors and detection rules.
Threat Hunting
Proactively hunt for advanced persistent threats using KQL queries, Jupyter notebooks, and machine learning insights.
Incident Response Automation
Automate incident response workflows with playbooks that can isolate endpoints, block IPs, and create tickets automatically.
Ready to Transform Your Security Operations with Microsoft Sentinel?
Let our Microsoft-certified experts implement a cloud-native SIEM solution tailored to your organization's needs.
Pay Only for What You Use
Microsoft Sentinel's data ingestion-based pricing model ensures you only pay for the security data you analyze
Pay-As-You-Go
Flexible pricing based on data ingestion volume
Included features:
Commitment Tier
Cost-effective pricing with volume commitment
Included features:
Enterprise
Tailored solutions for large-scale deployments
Included features:
Microsoft Sentinel vs Traditional SIEM
See why Microsoft Sentinel is the superior choice for modern security operations
| Features | Microsoft Sentinel | Traditional SIEM A | Traditional SIEM B |
|---|---|---|---|
| Cloud-native SIEM/SOAR | |||
| AI and machine learning | |||
| Pay-per-GB pricing model | |||
| Built-in Microsoft integrations | |||
| Automatic scaling | |||
| Built-in threat intelligence | |||
| No infrastructure management | |||
| Jupyter notebooks integration | |||
| 150+ data connectors | |||
| UEBA capabilities |
Why Choose GR IT Services for Microsoft Sentinel?
Real-world expertise from India cybersecurity challenges to enterprise-grade solutions
India Regulatory Compliance Expert
Deep understanding of India Central Bank cybersecurity regulations, ADGM data protection laws, and Hyderabad Financial Services Authority requirements. We ensure your Sentinel deployment meets all local compliance standards.
100% Compliance Rate
Microsoft Partner Status
As a Microsoft Partner in the India, we have exclusive access to Microsoft's advanced security resources, threat intelligence feeds, and early access to new Sentinel features and capabilities.
500+ Deployments Completed
24/7 SOC Operations Center
Our Hyderabad-based Security Operations Center provides round-the-clock monitoring and incident response. Native Arabic and English support ensures seamless communication during critical security events.
4.2 Min Avg Response Time
Real Success Stories from India Businesses
The Crisis
Manufacturing Company, Hyderabad
"Our existing SIEM was generating 15,000 alerts daily. Our security team was overwhelmed, missing critical threats while chasing false positives. We suffered a ransomware attack that cost us ₹2.3 crore in downtime."
Impact: ₹2.3 crore loss + 72 hours downtime
The Solution
After Microsoft Sentinel Implementation
"GR IT Services implemented Microsoft Sentinel with custom ML models for our manufacturing environment. Now we receive only 50 high-priority alerts daily with 98% accuracy. We prevented 3 advanced attacks in the first month alone."
Result: 99.7% threat detection + Zero breaches
300% ROI
Within 6 months of deployment
99.8% Uptime
Security operations availability
Zero Breaches
Since Sentinel deployment
Our Proven Implementation Process
Security Assessment
Comprehensive analysis of your current security posture and threat landscape
Custom Design
Tailored Sentinel architecture designed for your specific India compliance requirements
Deployment & Integration
Seamless integration with existing systems and gradual data migration
Training & Support
Comprehensive team training and 24/7 ongoing support from our Hyderabad SOC
Ready to Transform Your Security Operations?
Join over 500 India businesses that trust GR IT Services for their Microsoft Sentinel deployments
Experience Microsoft Sentinel's Intelligence
Watch how Microsoft Sentinel detects, investigates, and responds to threats in real-time
Threat Detection
Incidents detected: 1,247
AI Analysis
ML models running: 25
Automated Response
Playbooks executed: 342